Table of contents
Introduction
In the world of cloud computing, security is of paramount importance. Amazon Web Services (AWS) provides a powerful feature called Security Groups to help protect your cloud infrastructure. In this blog post, we will delve into the workings of AWS Security Groups, understand their significance, explore their practical applications, and examine real-time case studies to illustrate their effectiveness.
AWS Security Groups
AWS Security Groups act as virtual firewalls for your AWS resources, allowing you to control inbound and outbound traffic at the instance level. They provide a flexible and scalable means of implementing network security within your cloud infrastructure.
Security Groups are the fundamental of network security in AWS
• They control how traffic is allowed into or out of our EC2 Instances.
• Security groups only contain rules
• Security group rules can be referenced by IP or by security group
How AWS Security Groups Work
Security Groups are associated with AWS resources, such as EC2 instances or RDS database instances. They operate at the protocol and port level, allowing you to define rules to allow or deny traffic based on specific criteria. Inbound rules control incoming traffic, while outbound rules manage outgoing traffic.
Security groups act as a firewall on EC2 instances
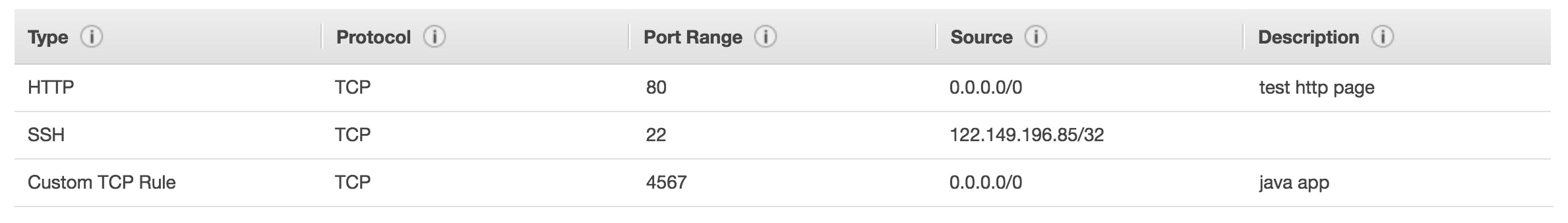
Access to Ports: Security groups control access to specific ports on EC2 instances. Ports are the virtual channels through which network communication occurs. Each port is assigned a number and associated with a specific protocol (e.g., TCP or UDP). By configuring security group rules, you can define which ports are open or closed for inbound and outbound traffic. For example, you can allow inbound access on port 80 (HTTP) to enable web traffic to reach your EC2 instance.
Authorized IP Ranges - IPv4 and IPv6: Security groups enable you to define authorized IP ranges or specific IP addresses that are allowed to access your EC2 instances. IP ranges are sets of IP addresses defined by their starting and ending points. By specifying these ranges, you can restrict access to your EC2 instances to trusted sources. This ensures that only authorized clients or networks can establish connections with your instances.
Control of Inbound Network (from other to the instance): Security groups control inbound network traffic, which refers to traffic coming from sources external to the EC2 instance. Inbound rules in the security group allow you to define which IP addresses, IP ranges, or security groups are allowed to access your EC2 instance and on which ports. For example, you can configure a security group to allow SSH access (port 22) only from a specific IP address or range, providing secure remote access to your instance.
Control of Outbound Network (from the instance to other): Security groups also regulate outbound network traffic originating from the EC2 instance and going to external destinations. Outbound rules in the security group define the allowed destination IP addresses, IP ranges, or security groups, along with the ports. By setting outbound rules, you can control which resources your EC2 instance can communicate with and on which ports. For example, you can limit outbound traffic to specific IP ranges or restrict access to certain protocols, enhancing the security of your instance.
Security groups act as a virtual firewall on EC2 instances, controlling access to ports, authorized IP ranges, and inbound and outbound network traffic. By carefully configuring security group rules, you can define the precise permissions for inbound and outbound connections, ensuring secure communication between your EC2 instances and the external network.
Remember to regularly review and update your security group rules to align with your evolving security requirements and to follow the principle of least privilege by only allowing the necessary access for your applications or services.
Use Cases and Practical Applications
AWS Security Groups find extensive use in various scenarios. They help secure web applications, enable multi-tier application architectures, control database access, and more. Let's explore some practical use cases:
Case Studies
Web Application Security
In a web application scenario, Security Groups can be used to restrict inbound access to HTTP (port 80) and HTTPS (port 443) traffic only from trusted sources. This ensures that your web servers are shielded from unauthorized access while allowing legitimate traffic.
Multi-Tier Application Architecture
For multi-tier architectures involving front-end web servers, application servers, and database servers, Security Groups can be utilized to enforce strict access controls between each tier. For example, the web server Security Group can allow traffic only from the application server, while the database server Security Group permits connections solely from the application server.
Database Access Control
In a database scenario, Security Groups can be employed to limit access to the database port (e.g., port 3306 for MySQL) to authorized clients or specific IP ranges. This prevents unauthorized access to sensitive data and protects the database from potential attacks.
Best Practices for AWS Security Groups
To maximize the effectiveness of AWS Security Groups, it is crucial to follow best practices. These include implementing the principle of least privilege, regularly reviewing and updating rules, monitoring network traffic, and leveraging other AWS security services like AWS Identity and Access Management (IAM) and AWS CloudTrail.
Conclusion
AWS Security Groups play a vital role in safeguarding your cloud infrastructure. By configuring well-defined rules, you can enforce granular access controls, protect sensitive resources, and mitigate security risks. Real-time case studies illustrate the versatility and practical applications of Security Groups in various scenarios.
In this blog post, we explored AWS Security Groups, their workings, and their significance in ensuring the security of your AWS resources. Understanding how to effectively leverage Security Groups is a crucial aspect of maintaining a robust and secure cloud infrastructure.
Remember to continuously evaluate and update your Security Group configurations as your cloud environment evolves and new security requirements arise. By following best practices and staying proactive, you can confidently protect your AWS resources from potential threats.
#AWS #SecurityGroups #CloudSecurity #InfrastructureProtection #RealTimeCaseStudies #NetworkSecurity #BlogPost